Computer Security at a New Low
Going Like Sixty — July 8, 2008 — Tech
References: blog.karppinen.fi
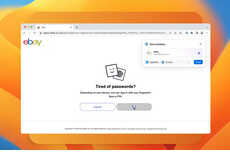
This is just so odd as to almost not pass the smell test. Apple support gave access to a computer via a request: "am forget my password of mac,did you give me password on new email marko.[redacted]@yahoo.com"
Marko Karppinen isn't just anybody. He is the head of a Mac software development company. So it's not that the hackers got access to view his collection of fish pron, there probably was some important stuff. Apple didn't raise an eyebrow, sending out the new access almost immediately.
Marko Karppinen isn't just anybody. He is the head of a Mac software development company. So it's not that the hackers got access to view his collection of fish pron, there probably was some important stuff. Apple didn't raise an eyebrow, sending out the new access almost immediately.
Trend Themes
1. Password Security Vulnerability - The trend of increasing online security threats requires enterprises to employ better password management systems and encourage better password habits among employees.
2. Improved Authentication Systems - Focusing on two-factor authentication and biometric verification technology can improve information security and reduce the risk of data breaches.
3. Cybersecurity Awareness Training - Companies are hiring experts to train employees on cyber threats and how to avoid them, supplementing automated security measures.
Industry Implications
1. Cybersecurity - Developers can create novel security solutions for both end-users and system administrators to prevent unauthorized access to sensitive data.
2. Software Development - Making products as secure as possible should be the top of the agenda for software development companies to avoid massive data breaches and to retain clients' trust.
3. Managed IT Services - As more and more companies seek managed IT services to handle their growing technical needs, MSPs can provide the expertise to help businesses understand the importance of password security and implement the best possible authentication systems.
1.4
Score
Popularity
Activity
Freshness